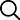
Three steps to establish IoT protection
发布时间:
2021-12-25
Developing and deploying an intelligent security architecture should focus on three steps: Know, Isolate, and Protect. Securing the IoT starts with understanding which devices can be trusted and managed, and which devices cannot be trusted, and untrusted devices are not allowed to access certain net
Developing and deploying an intelligent security architecture should focus on three steps: Know, Isolate, and Protect. Securing the IoT starts with understanding which devices can be trusted and managed, and which devices cannot be trusted, and untrusted devices are not allowed to access certain network partitions.
The Internet of Things (IoT) is one of the most important technologies in the current digital transformation (Digital Transformation) process, because an unprecedented amount of information can be collected through various connected devices, so that decisions can be followed by data before making decisions, thereby improving Business sales outcomes and quality of life.
However, over the past 12 months, we have continued to see cyberattacks targeting IoT devices continue to increase in frequency and sophistication. Unfortunately, too many IoT devices are never given serious security considerations. These devices are often headless devices with limited power and processing capabilities, which also means that it is impossible to install secure client software, further update applications or patch vulnerabilities. It’s no surprise that recent studies have shown that approximately 70 percent of IoT devices are highly vulnerable to cyber attacks.
As the Internet of Things (IoT) becomes ubiquitous, it puts pressure on security officers (CISOs), including other IT executives, to face growing security challenges. Every security officer has two goals: to increase productivity and maintain security. So how to balance business needs and security needs? Most of today's security systems are not enough to complete the security work independently. There must be a larger security architecture that is interwoven, interrelated, and information shared on the framework of its trust, and automatically protects and detects equipment and systems. Abnormal behavior; most importantly: automatically detects, audits and allows any new user or device connecting to the network, regardless of its physical location.
In simple terms, developing and deploying an intelligent security architecture should focus on three steps: Know, Isolate, and Protect. Securing the IoT starts with understanding which devices can be trusted and managed, and which devices cannot be trusted, and untrusted devices are not allowed to access certain network partitions.
1. Understand. Organizations must understand the capabilities and limitations of each device and network system. To do this, security solutions need to have full network visibility (Visibility) to authenticate and classify all IoT devices. Networks and devices of operational technology OT and industrial control systems ICS/SCADA are particularly sensitive because in some cases even simply scanning them can have negative effects. Therefore, organizations must adopt a trust-based security protection framework to automatically identify and classify devices in real time, create risk profiles, assign devices to IoT device groups, and dispatch appropriate security policies to security devices and network segments.
2. Isolation. Once complete visibility and centralized management are established, some IoT devices and communication solutions can be isolated in specific secure network segments through intelligent automatic control. This will automatically grant and enforce basic permissions based on each device's risk profile without compromising entire critical network systems.
3. Protection. The last is to combine the security policies of IoT device groups and intranet segments to implement multi-level monitoring, inspection and security policies, no matter where the activities occur in the distributed enterprise architecture.
Traditional single-point protection products and platforms are not enough to protect the IoT environment. Enterprises must establish a security architecture based on a trust framework and be able to interconnect with the Internet of Things and the cloud in order to automatically adjust and respond to evolving enterprise needs.
<The author Liu Yi is the technical director of Fortinet Taiwan>

Guangdong Joinet IOT Technology Co.,Ltd
生产制造基地:
Joinet Technology Park,No. 168 Tanlong North Road,Tanzhou Town,Zhongshan City,Guangdong Province,China
售前热线:19966308713 13823973022
总机电话:0760-8663 0003 (transferred) 523
售前邮箱:sw@znaiot.com


 粤公网安备44200002444728号
粤公网安备44200002444728号
联系我们:
随时期待您的来电